上個章節我們學習了Service的運用,並且也了解了kube-proxy、kube-dns的原理與運作。那在這章節中我們將學習如何使用loadBalancer與Ingress與外界溝通。
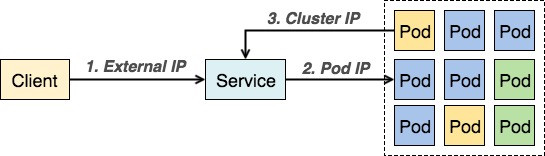
我們先來複習一下這個圖,從外界要與Pod溝通必經1與2兩條路。
也就是我們需要
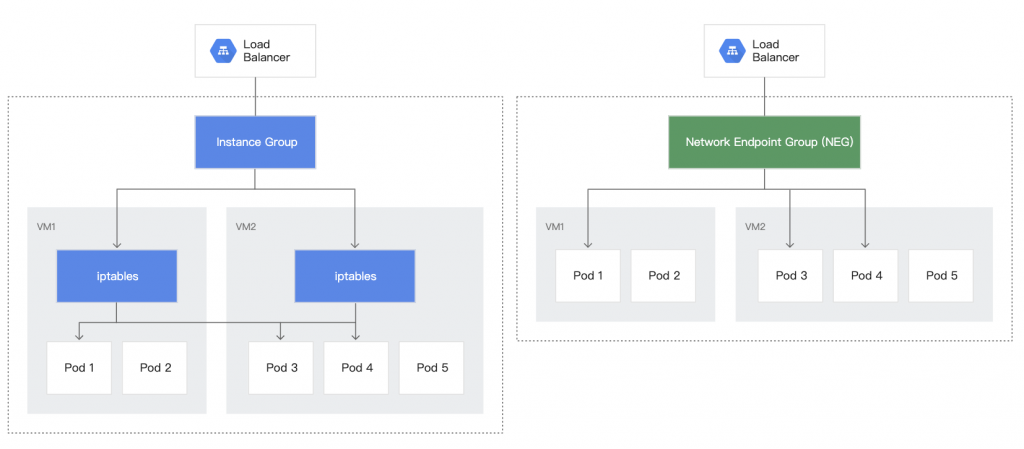
LoadBalancer屬於Service type的一種,也是其中一種暴露接口到Cluster外部的方式,他可以進行TCP/UDP的流量負載平衡與轉發,那並且LoadBalancer有著以下幾種特點:
那我們一樣,先寫好yaml再來解析它吧!
apiVersion: v1
kind: Service
metadata:
name: ironman
labels:
app: ironman
spec:
type: LoadBalancer
ports:
- name: http
port: 80
targetPort: 80
selector:
app: ironman
我們再來看一下建置好的結果吧!
$ kubectl delete service ironman
service/ironman deleted
$ kubectl apply -f loadbalancer.yaml
service/ironman created
$ kubeclt get service ironman
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ironman LoadBalancer 10.4.9.104 35.185.174.250 80:30445/TCP 5m58s
這邊可以看到我們建立了Service且
若想指定nodePort則像下方的寫法
apiVersion: v1
kind: Service
metadata:
name: ironman
labels:
app: ironman
spec:
type: LoadBalancer
ports:
- name: http
port: 80
targetPort: 80
nodePort: 32000
selector:
app: ironman
最後我們來GKE上看一下loadbalancer
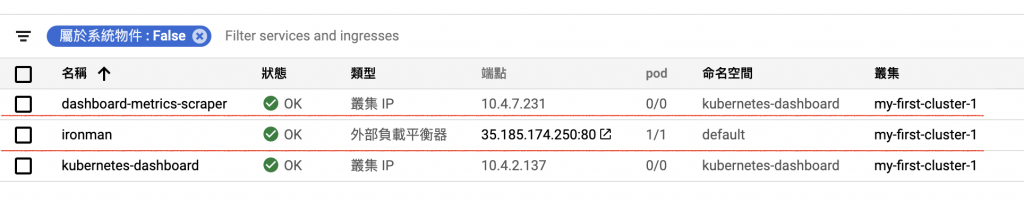
最後也確認了能夠透過外部ip去與pod溝通。
$ curl -X GET http://35.185.174.250/v1/hc
{"message": "This endpoint for web service health check"}
Ingress公布了cluster外部至內部的http與https routing。藉由ingress來定義routing rules。
所以Ingress能提供給我們
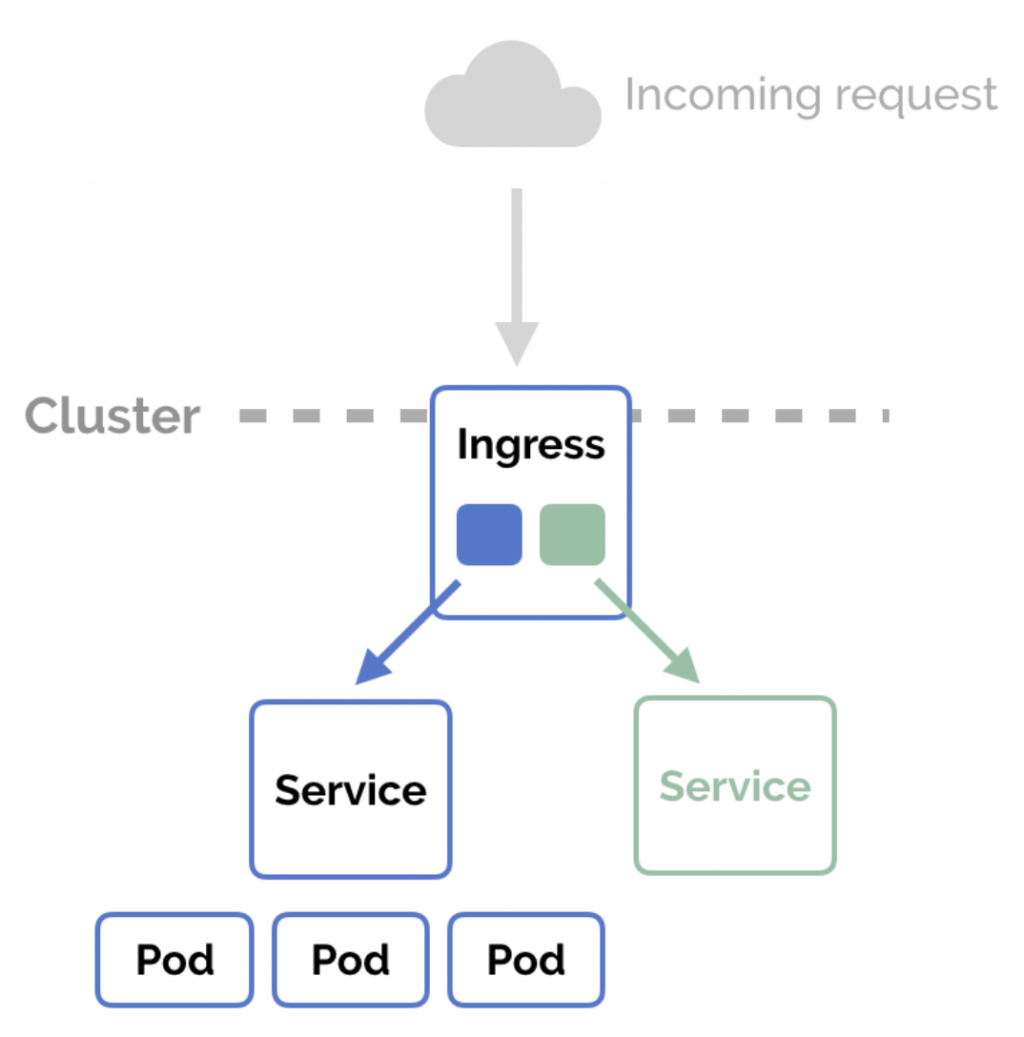
因為Ingress並不屬於service的一種,而是一種虛擬的託管物件,幫助service做負載平衡與ssl認證與黑白名單過濾...等功能。也因此在這個練習當中會有ingress與service兩個yaml
service.yaml
kind: Service
apiVersion: v1
metadata:
name: ironman
labels:
app: ironman
spec:
type: ClusterIP
ports:
- name: ironman
protocol: TCP
port: 80
targetPort: 80
selector:
app: ironman
ingress.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ironman-ingress
annotations:
kubernetes.io/ingress.global-static-ip-name: ironman
nginx.ingress.kubernetes.io/use-regex: "true"
spec:
rules:
- http:
paths:
- path: /v1
pathType: Prefix
backend:
serviceName: ironman
servicePort: 80
$ kubectl apply -f service.yaml
service/ironman created
$ kubectl apply -f ingress.yaml
ingress.networking.k8s.io/ironman-ingress created
$ kubectl describe ingress ironman-ingress
Name: ironman-ingress
Namespace: default
Address: <Address>
Default backend: default-http-backend:80 (10.0.1.4:8080)
Rules:
Host Path Backends
---- ---- --------
*
/v1 ironman:80 (10.0.2.11:80)
Annotations:
ingress.kubernetes.io/backends: {"k8s-be-31678--11092c602dd2be06":"Unknown","k8s1-11092c60-default-ironman-80-859c8e3a":"Unknown"}
ingress.kubernetes.io/forwarding-rule: k8s2-fr-e6h3ybgi-default-ironman-ingress-7xf4nxua
ingress.kubernetes.io/target-proxy: k8s2-tp-e6h3ybgi-default-ironman-ingress-7xf4nxua
ingress.kubernetes.io/url-map: k8s2-um-e6h3ybgi-default-ironman-ingress-7xf4nxua
kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"networking.k8s.io/v1beta1","kind":"Ingress","metadata":{"annotations":{},"name":"ironman-ingress","namespace":"default"},"spec":{"rules":[{"http":{"paths":[{"backend":{"serviceName":"ironman","servicePort":80},"path":"/v1","pathType":"Prefix"}]}}]}}
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal ADD 5m39s loadbalancer-controller default/ironman-ingress
Normal CREATE 4m46s loadbalancer-controller ip: <Address>
這邊可以看到我們建立了Ingress且
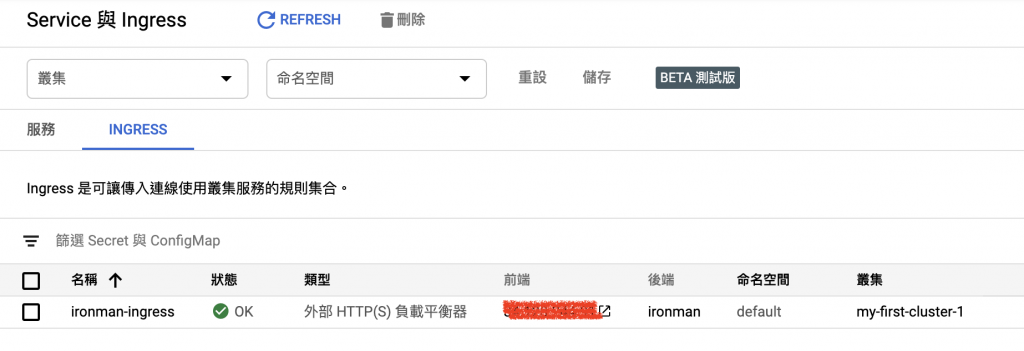
$ curl -X GET http://34.120.244.91/v1/hc
{"message": "This endpoint for web service health check"}
我們再來看一個比較艱深的例子吧
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ironman-ingress
annotations:
kubernetes.io/ingress.global-static-ip-name: ironman
spec:
tls:
- secretName: ironman-tls
rules:
- host: ironman2020
http:
paths:
- backend:
serviceName: ironman
servicePort: 80
https:
paths:
- backend:
serviceName: ironman
servicePort: 443
這邊我們多做了幾件事
(控制台—>VPC控制網路—>外部IP位置),請記得靜態Ip要先創建好否則ingress會mapping不到,這樣的話又會創一個臨時的靜態IP
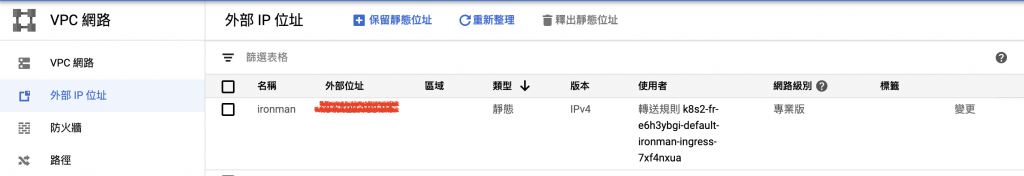
kubectl create secret tls ironman-tls --cert ironman_cert.pem --key ironmankey.pem
本篇章所有程式碼將放在下面的github project當中的branch day-22
這章節我們學會了如何使用LoadBalancer與Ingress,也讓我們的後端服務成功的與外界溝通,但我們現在使用的只是預設的Ingress Controller,且Ingress還有很多其他東西等著我們去挖掘。有時間的話我再額外開個篇章講述!
https://kubernetes.io/zh/docs/concepts/services-networking/ingress/
https://cloud.google.com/load-balancing/docs/network
https://kubernetes.github.io/ingress-nginx/
